Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DNS
Advanced DNS Protection: mitigating sophisticated DNS DDoS attacks
New Research: Spike In DNS Queries Driving Phishing and Cyber Attacks
Challenges and Recommended Best Practices to Secure DNS Infrastructure
Troubleshooting DNS issues in Kubernetes: Investigate and reduce NXDOMAIN (domain does not exist) responses
Cracking the Code: How to Identify Devices via MAC Addresses Online
Understanding DNS-Based Threats and How They Impact Your Business
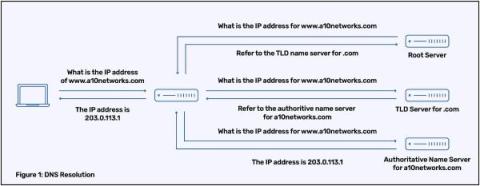
Cybersecurity, DNS (Domain Name System), and your company are interconnected topics in the field of network security. Protecting a company’s cybersecurity, including its DNS infrastructure, is of utmost importance in today’s digital landscape. DNS is responsible for translating user-friendly domain names into machine-readable IP addresses, allowing devices to communicate with each other over the internet.
How Egnyte Migrated Its DNS At Scale With No Service Disruptions
Egnyte, as a custodian of vast volumes of customer data and files, manages billions of files and petabytes of data originating from millions of users. With a system processing over a million API requests per minute, spanning metadata operations and analytical queries, the need to balance throughput and maintain exceptional service quality is paramount.