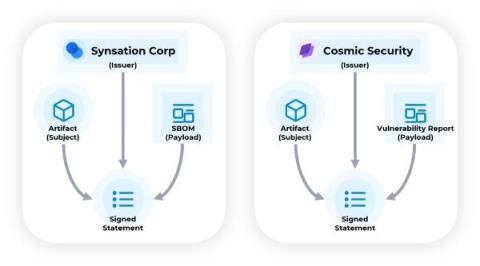
Secure Access To Your Software Development with GitHub OpenID Connect (OIDC) and JFrog
Modern software development requires a seamless connection between multiple software development tools – particularly those used for code management and storing your software artifacts. Connecting between these tools often involves managing a variety of tokens, permissions, passwords, and keys, which if not handled correctly can expose organizations to potential security threats.