Understanding Malicious Package Attacks and Defense Strategies for Robust Cybersecurity
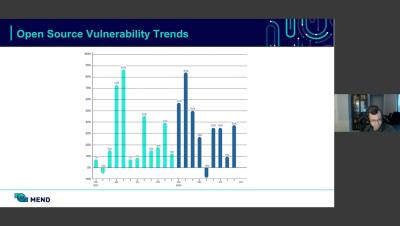
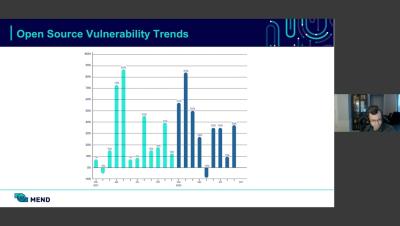
Malicious packages consist of software embedded with code that is capable of causing harm to an entire system or network. This is a rapidly growing threat affecting open-source software and the software supply chain. This attack method has seen a nearly 12,000% increase from 2022 to 2023, as reported by Synk. Some reasons include its technical feasibility, the potential for high returns, and the widespread distribution of open-source offerings, Common types of malicious packages encompass.