Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Encryption
Hardening Graylog - Encryptify Your Log Supply!
Disk encryption: the key to boosting your MSP service
Storing business data on personal devices and laptops has increased in recent years due to the shift towards hybrid or remote working models. This substantially raises the risk of sensitive information being exfiltrated if employees suffer theft, loss, or accidentally forget their devices.
How Diffie-Hellman Key Exchange Provides Encrypted Communications
The Twofish Encryption Algorithm
Introducing VM Encryption Detection
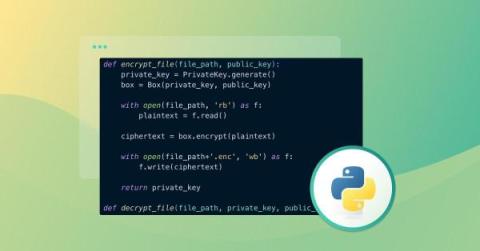
File encryption in Python: An in-depth exploration of symmetric and asymmetric techniques
In our modern world, we constantly share private, confidential, and sensitive information over digital channels. A fundamental component of this communication is file encryption — transforming data into an unreadable format using encryption algorithms.
Importance of Encryption in Messaging Apps
The Importance of SSL Certificate for an E-Commerce Website in 2024
Securing symmetric encryption algorithms in Java
In our connected world, securing digital data has become an utmost priority. With the wide spread of Java applications in various sectors, from banking to healthcare, we must emphasize the importance of encryption. Encryption is converting readable data or plaintext into unreadable data or ciphertext, ensuring that even if encrypted data is intercepted, it remains inaccessible to unauthorized individuals.