Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
AST
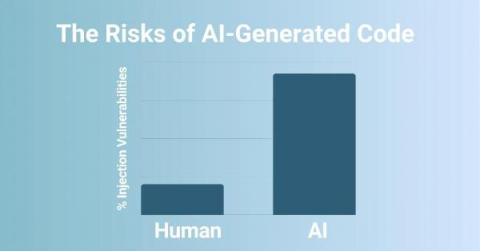
The Risks of AI-Generated Code
Synopsys and NowSecure join forces
Top Ten Tips to Choose a Great SAST Tool
Static application security testing (SAST) is a crucial component of any software and application security strategy, and as such, a SAST tool should form a valuable part of your security stack. But when you’re choosing which SAST tool to buy and implement, what are the key factors you should consider?
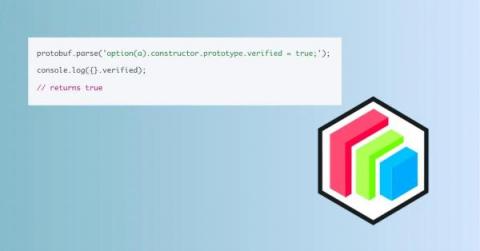
Code Intelligence Finds New Vulnerability in protobufjs: CVE-2023-36665
We benchmarked top SAST products, and this is what we learned
When we started to build Bearer, we wanted to understand how to validate the quality of our findings and be able to benchmark it. Code security scanning solutions are notorious for reporting a lot of false positives and other deficiencies, and even though we believed we could do much better, we needed a way to prove it. In Java, there is an OWASP project, BenchmarkJava, which makes it easy to compare the output of two software security solutions.