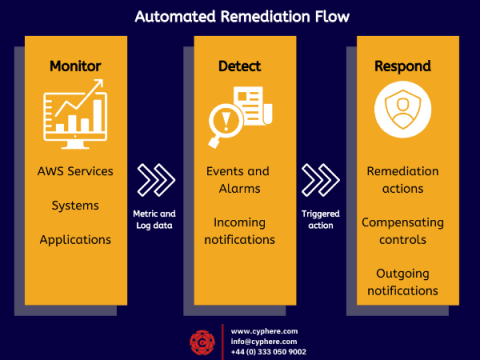
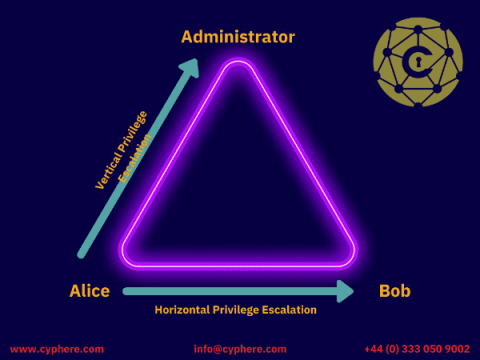
What is Typosquatting? Learn how to defend against it.
Typosquatting forms the basis of cyber attacks that aim to take advantage of users who mistake a malicious website for a legitimate one. Attackers register domain names that are similar to popular brands or products in the hopes that users will mistype the name and end up on their malicious site instead. Once on the site, users may be tricked into providing sensitive information or installing malware.