Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Zero Trust
Introducing ZTNA Next: Modern Security, Unprecedented Performance, and 100% Legacy VPN Retirement
In many conversations I have with security and infrastructure leaders, the discussion inevitably turns toward a zero trust project either already underway or set to begin soon. More often than not, this conversation is specifically about zero trust network access (ZTNA), because ZTNA technology has been frequently positioned as the solution for something every team really wants to achieve right now: total replacement of remote access VPNs.
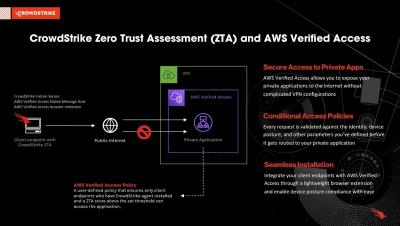
Securing private applications with CrowdStrike Zero Trust Assessment and AWS Verified Access
Securing private applications with CrowdStrike Zero Trust Assessment and AWS Verified Access
AWS Verified Access (AVA), a feature of Amazon Virtual Private Cloud (VPC) networking, delivers secure, zero-trust access to private applications without a VPN by continuously evaluating each request in real time based on contextual security signals like identity, device security status and location. The service grants access based on the security policy configured for each application and then connects the users, thereby improving the security posture of the organization.
The 443 Episode 238 - Zero Trust Maturity Model 2.0
How to Pitch Zero-Trust to Technology Executives
Why should organizations fund zero-trust architectures? The business benefits of zero-trust are significant. By adopting the "never trust, always verify" mindset, organizations shift to a more centralized security management approach, which can result in cost-effectiveness and a stronger layer of protection for resources such as identities, data, and applications.
Embracing Zero Trust for API Security
Driving Zero Trust Success in Government and Beyond
Tanium and Microsoft reveal more about their value-add for large organizations.