Preventing "copy-paste compromises" (ACSC 2020-008) with Elastic Security
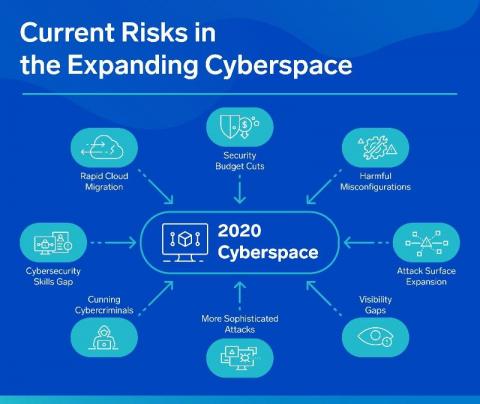
The Australian Cyber Security Centre (ACSC) recently published an advisory outlining tactics, techniques and procedures (TTPs) used against multiple Australian businesses in a recent campaign by a state-based actor. The campaign — dubbed ‘copy-paste compromises’ because of its heavy use of open source proof of concept exploits — was first reported on the 18th of June 2020, receiving national attention in Australia.