Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Logging
Logs Are Back-and Other Takeaways from AWS re:Invent
This month Devo exhibited at the AWS re:Invent conference in Las Vegas. I asked a few Devo colleagues who attended the show for their insights about what they heard and saw. Among the many visitors to the Devo booth there were a lot of similar questions about log management and related topics. “There were many log vendors at the show, so people wanted to hear what makes Devo unique,” said Seema Sheth-Voss, vice president, product marketing, for Devo.
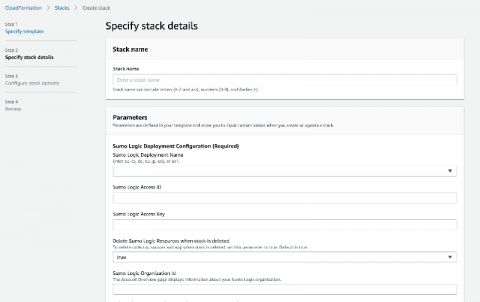
The New Sumo Logic AWS Security Quick Start
SOCtails Episode 2 - Automate your Security Operations
Considerations for taking the CompTIA Security+ exam
I recently took – and passed – the CompTIA Security+ exam (Sec+). Sec+ is a general introduction to multiple functional areas of security, ranging from network security to access control and identity management, for anyone looking to break into the space. For context, I have no previous training as a network or security professional, and my educational background was finance and Russian, nothing related to security.
Data Privacy Is Our Birthright - national cybersecurity month
SOCtails Episode 1
Why SIEM is here to stay: Part 2
Organizations are stretched thin managing increasingly complex environments and ever-expanding threat landscapes. At the same time, adversaries are becoming more organized and sophisticated, resulting in more complex and advanced threats. The current workflow in the Security Operations Center (SOC) – how data is analyzed and acted on – is simply not working. There are too many tools, not enough visibility, and burned-out analysts.