Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Blog
BMO Bank Loses Customer Data in Recent Data Breach Attack
BMO Bank is the 8th largest bank in the United States, employing over 12,000 individuals. The bank manages more than $3 Billion in annual reserves and works with a huge number of customers as it has over 1,000 physical locations across the country. BMO Bank is based in Chicago, Illinois, but has locations throughout the country. If you bank with BMO, your data may be at risk, because the organization was recently hacked and lost a significant amount of customer data.
Scalper Bots Jump on the Last Yeezy Drops
Scalper bots have had a busy year snatching and reselling Yeezy trainers, as adidas exhaust their final existing stock. This resulted in the Yeezy Slide Onyx topping the Netacea Quarterly Index of most-scalped items in Q2 of 2023.
Cyber Insurance Claims Increased by 12% in First Half of 2023, Attacks More Frequent and Severe Than Ever
The latest cyber claims report from Coalition, a digital risk insurance provider, finds a 12% increase in cyber insurance claims in the first half of 2023 over the second half of 2022, due to surging attack frequency and severity. No industry or company size is immune as the increase was seen across all organizations, however companies with $100 million in revenue saw the largest increase in number of claims (+20%), as well as staggering losses resulting from attacks (+72%).
API Security Trends 2023 - Have organizations improved their security posture?
APIs, also known as application programming interfaces, serve as the backbone of modern software applications, enabling seamless communication and data exchange between different systems and platforms. They provide developers with an interface to interact with external services, allowing them to integrate various functionalities into their own applications.
What Does Secure by Design Actually Mean?
In this era shaped by digital innovation, the concept of Secure by Design is a critical safeguard against cyber threats. Read on to delve into the essence of Secure by Design and its profound relevance in today's technology landscape. As cyberattacks grow more sophisticated, comprehending the proactive principles behind secure design is paramount to ensuring a resilient and protected digital future.
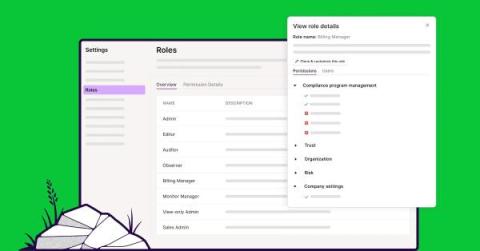
Introducing expanded Role-Based Access Control
Today we’re thrilled to announce that Vanta’s Role-Based Access Control (RBAC) functionality has gotten even stronger with new capabilities, including: These expanded RBAC capabilities are now generally available and demonstrate Vanta’s continued commitment to supporting the needs of larger, more advanced organizations through additional customization and flexibility across our platform.
Weekly Cyber Security News 28/09/2023
A selection of this week’s more interesting vulnerability disclosures and cyber security news. Back again in the news but with a different twist….
SIEM vs. SOAR in 2024: What's The Difference?
Introducing Jobs-to-be-Done: a way to help our users achieve their goals
As a security practitioner, the scope and responsibilities of your role have likely changed over the last few years. This is likely an accumulation of: But what hasn’t changed? Regardless of any new scope or responsibilities, you still have a set of things you need to accomplish and get done that are the most important to you.