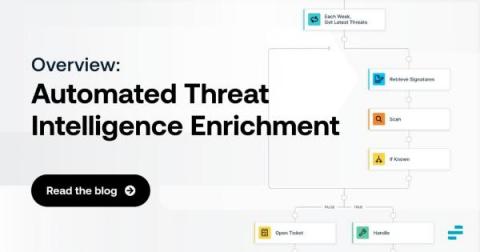
How Chatbot Automation Benefits Security Teams
When you hear the term “chatbot,” your mind may at first turn to things like robotic customer support services on retail websites – a relatively mundane use case for chatbots, and one that is probably hard to get excited about if you’re a security engineer. But, the fact is that chatbots can do much more than provide customer support.