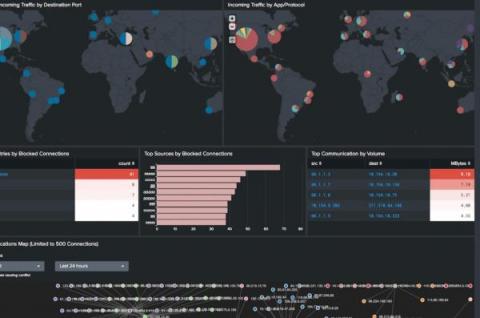
Splunk Security with the Infosec App
There's so much that can be accomplished with Splunk’s security tools. Today, we are going to focus on all the benefits of the InfoSec App for Splunk. The InfoSec app — which is an entitlement to Splunk customers — is powered by the Splunk platform, and relies on accelerated data models and the Common Information Model (CIM) to provide a consistent and normalized view into the event data that you’ll bring into Splunk.