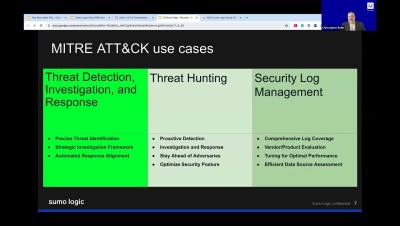
What is the MITRE ATT&CK framework?
As a kid, treasure hunts were fun. Someone gave you clues and a map so you could hunt down whatever hidden item they left for you. However, as a security analyst, your incident investigations often have clues but lack a map. An alert fires. You search through your vast collection of log data. You hope to find the next clue while trying to figure out the attacker’s next steps.