What Is Integrity Management?
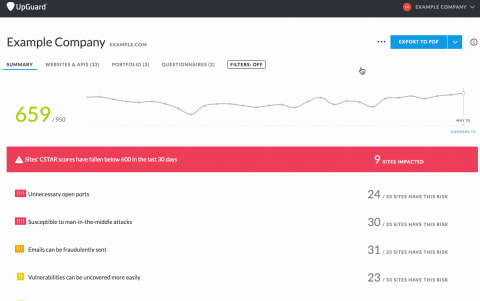
If you’ve been in information security for a while, you’ve likely had some experience with file integrity monitoring (FIM). It’s a capability with a long history, going back to the original open-source Tripwire tool for monitoring file hashes. And FIM has staying power. It’s still around, and there are still new deployments. There aren’t a lot of security controls that continue to be valuable over such a long time frame.