Introducing DataTrails provenance automation for Dropbox files
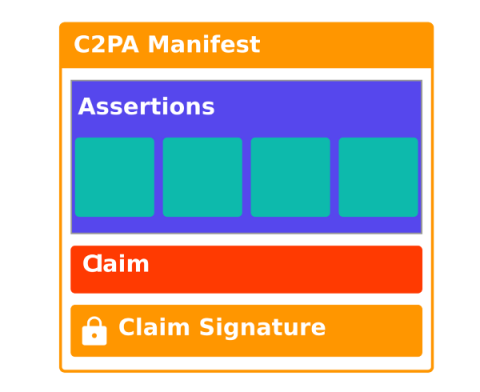
We are thrilled to announce a new integration with Dropbox that enables verifiable provenance metadata to be automatically created for content you store and manage on Dropbox. With the onset of generative AI and the increasing threats of fake data and fraud, the ability to prove ownership of your content and protect it from misuse is more urgent now than ever.