Rethinking Privileged Access Management for Cloud and Cloud-Native Environments
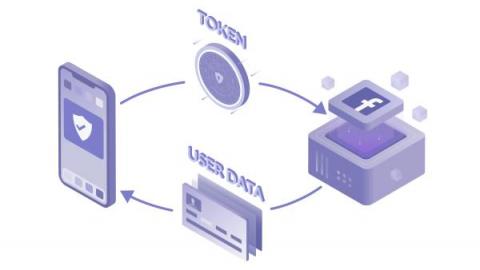
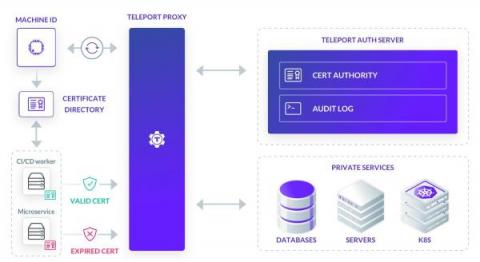
SSH was designed in 1995, LDAP was initially developed in 1993, and role-based access control was introduced in 1992. The concept of least privilege was introduced in 1975. With all of these existing technologies, when are modern privileged access management solutions necessary? This is a common question asked when we pitch the idea of modern privileged access management (PAM).