Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevSecOps
[Webinar] DevSecOps - A DevSecOps Maturity Model for Secrets Management
Veracode Launches Container Security Offering That Secures Cloud-native Application Development
8 Essentials for Automated DevSecOps Compliance
In the last decade, there has been an increasing focus on compliance and security. As a result, regulatory bodies have established severe penalties for non-compliance. Consequently, organizations put together compliance frameworks that are pertinent to their industry. To support such frameworks, security tool vendors have developed solutions to help these organizations easily automate security compliance.
API Security for DevSecOps
DevSecOps is a variant of DevOps that adds security to the software development workflow. Application Programming Interfaces (API) security needs to be part of DevSecOps. This article explores how DevSecOps works and the role that API security plays in making applications that result from DevSecOps as secure as possible.
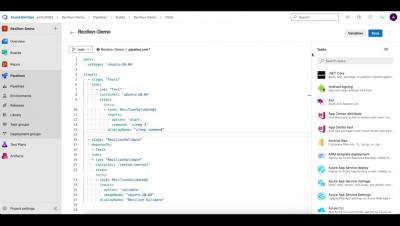
Rezilion-Azure DevOps Integration
Healthcare Sector Leads The Way For Fix Rate Of Software Security Flaws
Organizations Want to Adopt DevSecOps. What's Getting in Their Way?
Security leaders are eager to move to a DevSecOps approach—and why wouldn’t they be? DevSecOps has been emerging as a key component in organizations’ efforts to build strong security into all the software products they deliver. The adoption and implementation of the DevSecOps methodology involves multiple facets of organizations and brings together security and development professionals in a collaborative mission to deliver products that are both high in quality and secure.
Rezilion and CircleCI Integration Demo
Response to the Enduring Security Framework (ESF) Guide for Developers
At Snyk we invented developer-first security. We believe involving developers in the practice of security is key to building and running modern applications. This is exactly why the recent publication, Recommended Practices Guide for Developers by the The National Security Agency (NSA), Cybersecurity and Infrastructure Security Agency (CISA), and the Office of the Director of National Intelligence (ODNI) piqued our interest.