New Platform Features: Spring, 2023
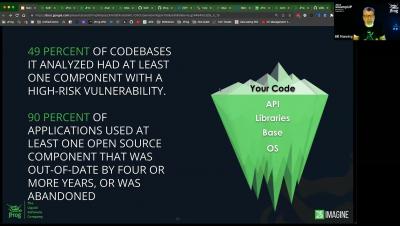
As Head of Product at Rezilion, I am excited to share some of the new features and enhancements we have added to the platform in the first few months of 2023. With these new features, you’ll be able to effectively manage your supply chain risks with more visibility, accuracy, and convenient automation than ever before.