Version Control Best Practices With Teleport RBAC Roles
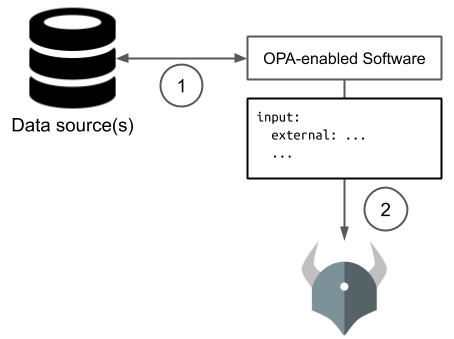
Imagine you've just deployed a working Teleport cluster and you're making changes to the Role Based Access Controls (RBAC) roles, fine-tuning all of your resource permissions, and making sure every role is following the principle of least privilege. You go for a week-long vacation, do some fishing and completely relax. Getting back you find that the DevOps intern you just hired made a bunch of changes to the roles screwing everything up.