All the Proxy(Not)Shells
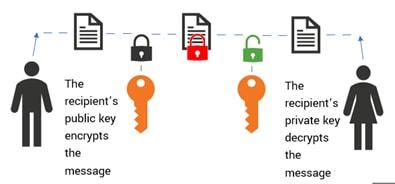
On September 28th it was disclosed by GTSC that there was a possible new zero day being abused in the wild beginning in early August. Although this campaign looked very similar to the previously abused vulnerability in Microsoft Exchange, dubbed ProxyShell at the time, comprising 3 CVEs (CVE-2021-34473, CVE-2021-34523 and CVE-2021-31207) that when combined enabled an adversary to gain remote access to an Exchange PowerShell session that may be abused.