Password Length vs Complexity: Which Is More Important?
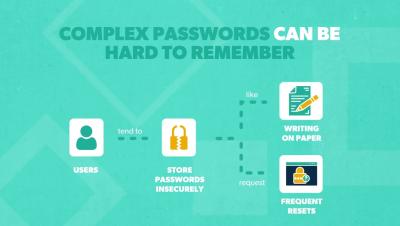
In this video, learn about the differences between password length and complexity, which is more important, and four tips to improve password security in your organization. Learn more about: Resources and social media: Transcript: It’s no secret that passwords aren’t foolproof. In fact, the most common way that hackers infiltrate an organization is through stolen credentials. But until the day that everything has shifted to passwordless authentication, passwords are still necessary. So, how can we make them as strong and effective as possible?