Practical advice to secure your expanding attack surface
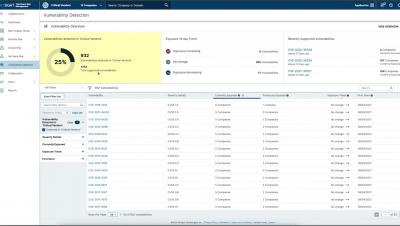
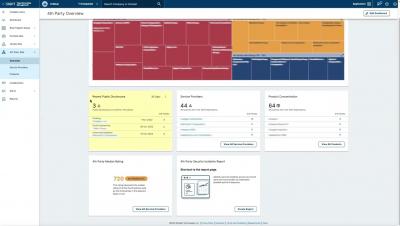
The other week, BitSight published research identifying thousands of organizations using internet-facing and exposed webcams with many video and audio feeds susceptible to spying. The potential consequences are serious – an attacker could potentially view private activities and eavesdrop on sensitive conversations, presenting a variety of privacy and security concerns. Below are some of the screenshots BitSight captured from exposed devices (blurred for privacy).