Navigating the Shift: From Vulnerability Management to Continuous Threat Exposure Management
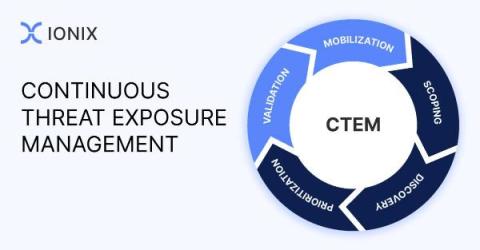
In the rapidly evolving cybersecurity landscape, organizations face an ever-increasing barrage of threats. Traditional vulnerability management, while foundational, often falls short in proactively and continuously identifying and mitigating threats. This necessitates a paradigm shift towards Continuous Threat Exposure Management (CTEM), a more dynamic approach that aligns with the complexities of today’s digital environments.