Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Kovrr
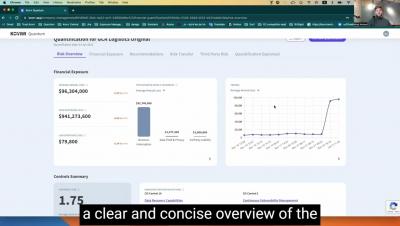
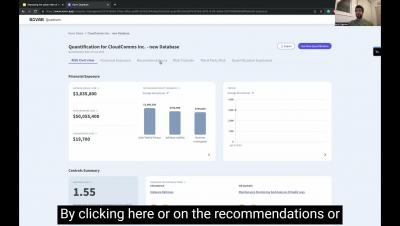
New Feature: NIST CSF Mitigation Recommendations
Does your organization currently speak in the NIST framework language? Say bye-bye to manual mapping and say HELLO to filling out inputs in the NIST CSF framework. This new release helps security teams better align with the organization’s internal communications around security controls. We know that staying consistent with the company’s terminology can better help you achieve your goals.
January Cyber Roundup
T-Mobile has once again fallen victim to a massive new cybersecurity breach, discovered on Jan. 5. The company has a history of hacks from recent years, for which it was fined hundreds of millions of dollars. Using weak API security, the attack caused the exposure of the personal data of more than 37 million customer accounts, which was apparently first accessed on or around Nov. 25. The stolen records include addresses, phone numbers and dates of birth.
Why Hackers Love Credentials: Parsing Verizon's 2022 Breach Report
The 2022 Verizon Data Breach Investigations Report (DBIR), the fifteenth such report in as many years, leads off with a startling statistic: Credentials are the number one overall attack vector hackers use in data breaches. Use of stolen credentials accounts for nearly half the breaches studied by Verizon, far ahead of phishing and exploit vulnerabilities, which account for 19% and 8% of attacks, respectively. Botnets, the fourth most common entry path for hackers, represent a mere 1% of attacks.