Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Sedara
Succeeding at Cloud Vulnerability Management
NIST CSF 2.0 is Here. What do You Need to Know?
How to Build a Cybersecurity Awareness and Training Program
So, You Want to be Compliant. Now What?
What is a Cybersecurity Development Program and how does it work?
Highlights from The Rochester Security Summit 2023
October’s a fun month in the cybersecurity field, and not just because of the costumes and candy. Since it was designated as the National Cybersecurity Awareness Month in 2004, October’s always packed with great events, such as the Rochester Security Summit (RSS). RSS has been a leading regional cybersecurity conference in Upstate New York since 2006, where hundreds of attendees gather to share about the latest advancements in the field.
Using "Canaries" to Detect Intruders
Staying ahead of potential threats and breaches is a constant battle. One innovative solution is the use of “canaries” to detect attempted intrusions. Canary assets are one clever way to detect intruders in your network.
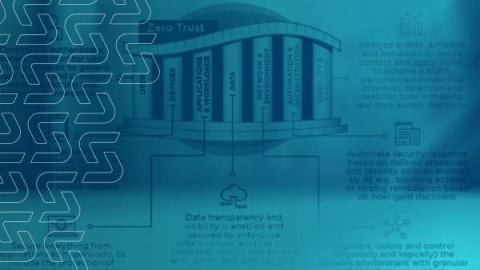
What is Zero Trust
Zero Trust is a cybersecurity philosophy that rejects the idea of offering implicit trust to traffic based on network location. In other words, Zero Trust views all traffic as potentially malicious, regardless of whether it originates from a traditionally trusted network source, and therefore requires all traffic to be scrutinized to determine whether access should be granted to a specific resource.