The JFrog Platform Delivered 393% ROI
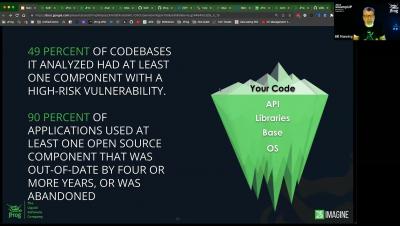
I’m excited to share the findings of a Forrester Consulting Total Economic Impact™ (TEI) study, a recently commissioned study conducted by Forrester Consulting on behalf of JFrog, which examines the potential return on investment (ROI) that organizations may realize by deploying the JFrog Software Supply Chain Platform. Software has become the critical infrastructure of our daily lives.