AWS threat emulation and detection validation with Stratus Red Team and Datadog Cloud SIEM
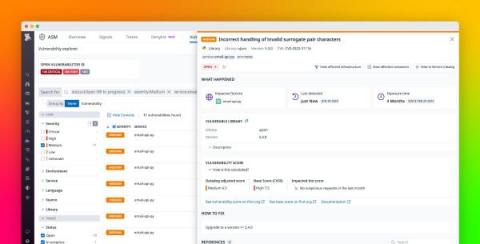
As attackers get more creative in their malicious tradecraft, cloud security teams must be able to keep up with detections that provide adequate coverage against the diverse threats to their cloud environments. Threat emulation enables cloud security teams to leverage their understanding of threat actor behaviors as a feedback loop for developing cloud-based detections and validating their resilience.