Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
LogSentinel
LogSentinel XDR - A Unified Security Monitoring Platform
XDR (eXtended Detection and Response) is a new Gartner category, which, we’ve argued before, is SIEM++, or what next-gen SIEM should have been. This is why we are packaging our latest feature updates into an XDR offering that should greatly improve the detection and response capabilities of any organization, especially mid-market organizations, which gain the most benefit from integrated, easy-to-use platforms. LogSentinel XDR is a unified security monitoring and response platform.
Why is LogSentinel a Great Fit to Any MSSP?
On the shifting threat landscape, security investments are growing, the complexity of security solutions continues to increase, hence the need for managed security service providers (MSSPs) will continue to grow proportionally.
LogSentinel SIEM for MSSPS: Key MDR / MSSP Benefits
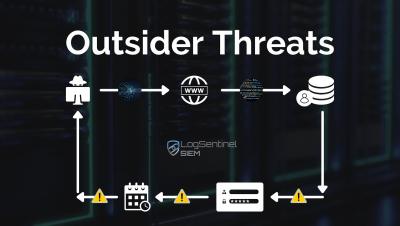
Case Study: Outsider Attacks - Before and After LogSentinel SIEM
Case Study: Insider Attacks Before and After LogSentinel SIEM
How to Detect Office 365 Anomalies Using SIEM
Microsoft Office 365 (also known as Microsoft 365 or Office 365) is a cloud-based service that enables online collaboration and real-time data sharing via Microsoft solutions such as SharePoint, MS Teams, and OneDrive. Microsoft Office 365 brings together familiar Microsoft Office desktop applications together with business-class email, shared calendars, instant messaging, video conferencing, and file sharing, making it an integral part for many in times of pandemic.