Zero Trust and (Why It Isn't Always About) Identity
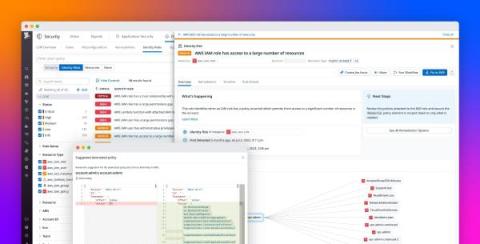
What is the relationship between zero trust and user identity? There’s no doubt that identity is a fundamental component of an effective zero trust approach, but there is also a danger that organisations become so overly focused on this one element, they forget there are others. To believe that achieving zero trust is all about user identity is, I believe, a fundamental misunderstanding of the concept.