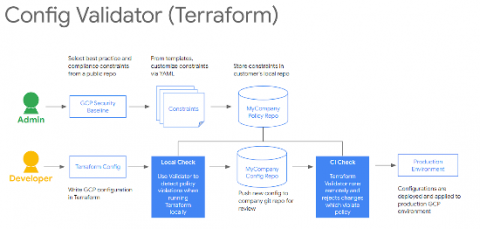
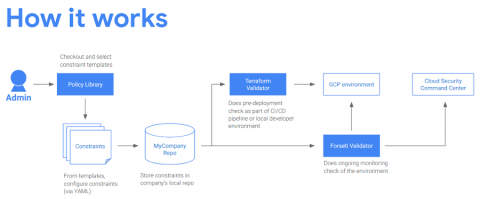
Google Cloud Platform compliance & Risk Management
Previously we published an article discussing some of the best practices surrounding cloud security, in this article, we will discuss cloud a little more specifically by focusing on one in particular provider Google. Google offers several different solutions for customers known as GCP or the Google Cloud Platform. GCP is set infrastructure tools and services which customers can utilize to build environments they need in order to facilitate a solution for their business.