|
By Terry Young
Recently a large service provider in Eastern Europe contacted the A10 threat research team for insight into a series of DDoS attacks against its network. While the attacks were not service impacting, the frequency and persistence of the attacks raised internal concerns that the attacks might mask a more malicious intent: could this be a state actor planting malware or testing their defenses for a larger attack against critical infrastructure?
|
By Gokul Pokuri
In today’s rapidly evolving digital and cyber landscape, securing and delivering applications efficiently is crucial for businesses of all sizes. The pursuit of uninterrupted service is no longer the only focus. Security concerns have taken center stage, transforming the landscape into a battleground where the slightest disruption triggers a search for root causes and solutions. When websites falter, application owners navigate a maze of possibilities.
|
By Gary Wang
An addition to the A10 Defend suite has arrived. A10 Defend Threat Control, a necessary and proactive DDoS intelligence SaaS platform, is here to establish and amplify your holistic DDoS defense system. Backed by A10’s proprietary “zero-atrophy” data gathering and validation method, Threat Control provides actionable insights and proactively establishes a first layer of defense for your DDoS protection needs.
|
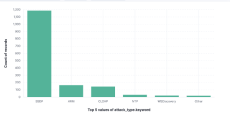
By Rich Groves
The attacks are ongoing as of this writing. Here are a few screenshots of data and some insight. I’ll make sure to keep it brief since you have seen this news in various outlets.
Featured Post
The UK's 2023 National Risk Register, published by the government in the summer, highlights the increasing cyberthreat posed to telecommunications providers who are a vital part of the communications critical national infrastructure (CNI) sector. The report lays out the volatile landscape these providers operate in and the government's acknowledgement of the seriousness of cyber threats to telecommunications infrastructure. It also details the difficulty in implementing the Telecommunications (Security) Act 2021, which establishes guidelines for telcos to follow.
|
By Terry Young
Federal and private funding, new market entrants, and creative problem-solving have made it possible to extend broadband connectivity to more U.S. households than ever. But as regional and rural broadband providers, electric utilities and co-ops, satellite operators, and others push to fully close the digital divide, a remaining challenge looms: ensuring enough IP address space to support this growing subscriber base.
|
By Andrew Gibson
A10 Networks has expanded its robust application delivery controller (ADC) solution to Google Cloud Platform (GCP), meeting the increasing demand for powerful and scalable application delivery in the cloud. Customers can now rapidly deploy A10 Thunder® ADC on GCP via the Google Cloud Marketplace.
|
By Gary Wang
Distributed denial of service (DDoS) attacks have consistently been a chief concern of security teams. However, common misconceptions still exist. Some view that DDoS attacks are merely nuisances or inconveniences – that they are volumetric and straightforward to defend against – and that the DDoS defenses most organization use today are fully capable of rendering these threats obsolete.
|
By Vishnu Vasanth Radja
The A10 Networks threat research team has investigated the HTTP/2 rapid reset vulnerability ( CVE-2023-44487), which has been identified in recent days and has advised customers on the best ways to mitigate it in their network.
|
By Gary Wang
In today’s world, and in particular, the cybersecurity landscape, the buzzword is undoubtedly “AI.” We’re constantly discussing it because of its incredible ability to think, create, and adapt in real-time.
|
By A10 Networks
A10 Defend Threat Control provides a robust first layer of DDoS defense. By leveraging proprietary ML/AL-enhanced data processing techniques, Threat Control proactively monitors attackers and understands key DDoS attack methods, with or without dedicated DDoS prevention solutions.
|
By A10 Networks
The transition from IPv4 to IPv6 won't happen overnight—but it doesn't have to be an ongoing headache. Learn how you can bridge the shift from IPv4 to IPv6 with a lifecycle strategy that meets both short-term needs and long-term requirements for your customers, subscribers and business.
|
By A10 Networks
As the world experiences uncertainty stemming from economic, social, and geopolitical disruption, digital connectivity has never been more important to address inequality, support communities and drive global business recovery. This survey interviewed 2,750 communication service provider IT professionals. Respondents come from a broad range of provider types, data center/co-location, service providers and fixed wireless access providers.
|
By A10 Networks
A10 Next-Gen WAF, powered by Fastly, leverages advanced technology to protect web applications from complex modern threats while minimizing false positives and ensuring availability. See how our integrated Next-Gen WAF, enabled on Thunder ADC, effectively blocks attacks while remaining user-friendly. Get insights into its visibility, DevOps, security tool integrations, and analytics features for advanced web application protection.
|
By A10 Networks
Cyber criminals are individuals or groups of people who use computers and networks to commit online crimes. Sometimes using malware programs, they aim to harm other individuals, companies, and governments. Though their methods are varied, cyber criminals frequently employ ransomware, holding your data hostage; and data exfiltration, the unauthorized extraction of your data. Guarding against cyber crime requires the awareness and participation of everyone in an organization.
|
By A10 Networks
An infrastructure attack aims to exploit vulnerabilities in the network layer or transport layer. These attacks are called DDoS attacks and include SYN floods, Ping of Death, and UDP floods. Infrastructure attacks can be broken down into two subcategories: volumetric attacks and protocol attacks. Volumetric attacks focus on inundating a server with false requests to overload its bandwidth, while protocol attacks target specific protocols to crash a system.
|
By A10 Networks
Protecting your company's data is crucial, whether in transit, stored in a device, or a cloud-based repository. One effective way to safeguard against potential threats is through encryption. Encryption involves scrambling your data to become unreadable if it falls into the wrong hands.
|
By A10 Networks
Data breaches can take many forms, from an unintentional release of information by an unaware employee, to a cyber criminal using stolen login credentials to access sensitive data to a ransomware attack that encrypts a company's confidential information. The types of data that can be involved also vary; it can be personal health information, such as medical records; personally identifiable information like driver's license numbers, financial information, such as credit card numbers; and trade secrets and intellectual property like product designs.
|
By A10 Networks
A significant milestone occurred with the reported largest DDoS attack on Amazon Web Services (AWS) reaching 2.3 terabits per second. This is a substantial increase of 70% from the previous record holder, the Memcached-based GitHub DDoS attack in 2018, which measured 1.35 terabits per second. Over the years, these attention-grabbing performance gains in DDoS attacks have been rising consistently, with major high-profile attacks happening every two years.
|
By A10 Networks
The term of the day is DDoS-for-hire, a service that allows anyone to purchase and carry out a distributed denial of service (DDoS) attack. This type of service is modeled after the Software as a service (SaaS) business model and is often profitable because it allows the operator of an Internet of Things (IoT) botnet to conduct a cost-effective attack.
|
By A10 Networks
Domain Name System (DNS), often referred to as the "phonebook of the internet," is an important protocol for the overall functioning of the internet, translating domain names into IP addresses and vice-versa. DNS, though, is an inherently insecure protocol and is vulnerable to a variety of cyberattacks that can disrupt network and service availability and violate confidentiality of users and their data. This poses a challenge for the teams responsible for ensuring uninterrupted DNS service and maintaining user privacy.
|
By A10 Networks
Secure application delivery in a hybrid cloud environment is the foundation of modern digital business-but it also poses significant challenges. There's more than one way to go hybrid cloud. To meet the challenges of a hybrid cloud environment, many organizations are now adopting a cloud operating model. The goal is to use technology to create a secure, flexible, scalable, and agile IT infrastructure that can support business growth and innovation while optimizing cost efficiency. But achieving these goals can be a challenge.
SDxCentral Solution Guide: How to Ensure Effective and Secure Application Delivery in a Hybrid Cloud
|
By A10 Networks
Enterprises have been moving to hybrid cloud environments for years, whether for cost savings, data sovereignty, or geographic reasons. As IT environments grow increasingly complex, and security and compliance continue to present new challenges, many organizations are looking for a more effective approach to application delivery.
|
By A10 Networks
A Zero Trust Approach to Protect Data Privacy Data protection in healthcare is critical. From the hospitals at the front line, to the insurance providers behind the scenes, all such organizations bear the dual responsibility of protecting themselves, as well as their patients. They must safeguard their data privacy, identity, security, and finances of their patients. They must also protect their own organization from costly breaches, regulatory fines, and damage to their business, reputation, and patient relationships.
|
By A10 Networks
Not that long ago, organizations were squarely focused on moving their applications and infrastructure to the cloud to benefit from its scalability, flexibility, and cost savings. Today, however, priorities are shifting, leading many to focus on right-sizing hybrid cloud deployments and establishing digital resilience. You will learn how digital resilience for hybrid cloud application delivery.
- April 2024 (1)
- March 2024 (4)
- February 2024 (5)
- January 2024 (1)
- December 2023 (1)
- November 2023 (1)
- October 2023 (2)
- September 2023 (1)
- August 2023 (4)
- June 2023 (2)
- May 2023 (1)
- April 2023 (1)
- January 2023 (12)
A10 Networks provides security and infrastructure solutions for on-premises, hybrid cloud, and edge-cloud environments. Our 7000+ customers span global large enterprises and communications, cloud and web service providers who must ensure business-critical applications and networks are secure, available, and efficient.
Why Customers Choose A10:
- Industry-leading Performance: Fastest response and lowest latency for mission-critical applications.
- Comprehensive and Integrated Security: Including options for next-gen WAF, DNS application firewall along with integrated DDoS protection.
- Simple Operations for Predictable OPEX: With all-inclusive license and flexible scale-out across multi or hybrid clouds.
- World-class Customer Support: With available and committed team for support when you need it.
Eliminate Costly Downtime, and Risk of Revenue Loss.