Post-perimeter security 101: Dawn of a borderless world
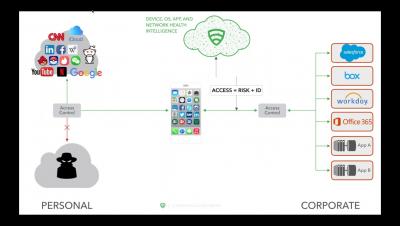
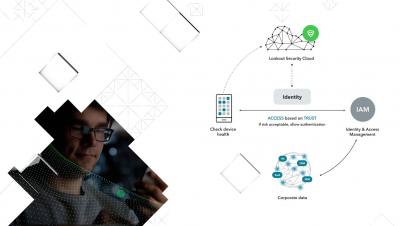
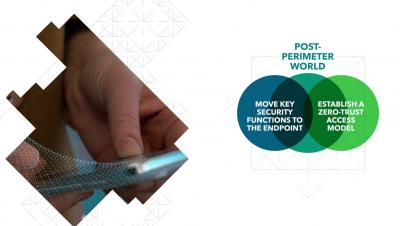
The perimeter has disappeared. Employees work from anywhere in the world and their devices access corporate data from cloud services outside of traditional security perimeters. Securing data in the post-perimeter world requires organisations to enforce their endpoints and establish continuous conditional access to data based on risk. Aaron Cockerill, Chief Strategy Officer at Lookout discusses how to effectively shift security to your mobile endpoints to protect your company’s sensitive data.