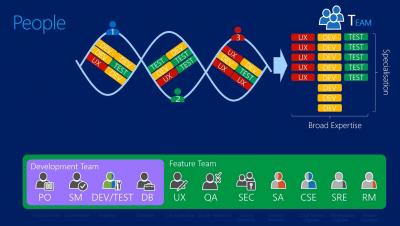
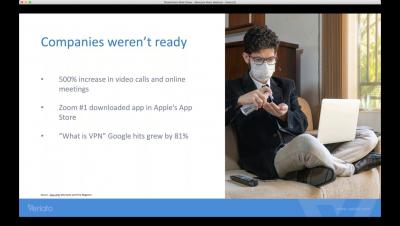
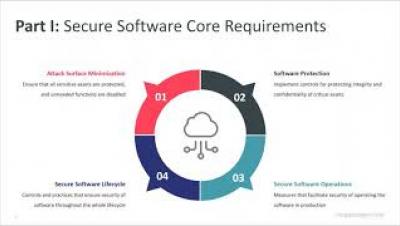
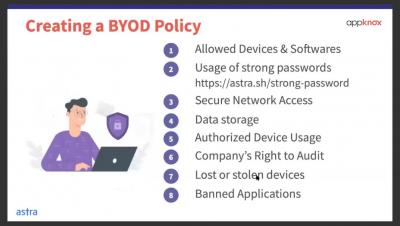
Whose vulnerability is it anyway?
Application security is a top priority today for companies that are developing software. However, it is also becoming more challenging and complex as release frequency continues to rise, more open source components are adopted, and the requirements for data security are getting stricter. Thanks to new DevOps practices and tools, development cycles are getting shorter, allowing organizations to meet market demands and deliver a superior customer experience, but is application security keeping up?