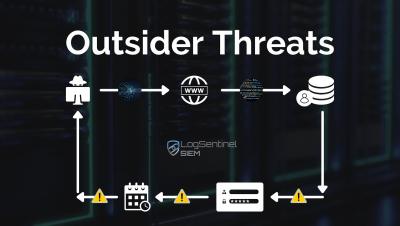
3 Cases of Hacked IoT Devices -- LogSentinel
internet of Things is a network of interconnected devices, software, sensors, or people that are provided with unique identifiers (UIDs), with the ability to transfer data over a network without the need for human interaction. Many #IoT devices remain unmonitored and improperly managed. These risks can become life-threatening when it involves the #healthcare sector. LogSentinel presents 3 notorious cases of hacked IoT devices and ways to keep your IoT devices safe. Monitoring threads and mitigating the risk for #cybersecurity in your organization is crucial.