Job-to-be-Done: Understand what is being continuously tested and monitored across my attack surface
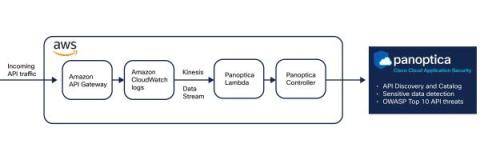
In order for AppSec and ProdSec teams to stay on top of their growing attack surface, they must understand what parts of their attack surface are being continuously monitored and scanned, such as where, when, what, and how. This can include, but is not limited to.