Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
API Security Standards and Protocols: A Primer
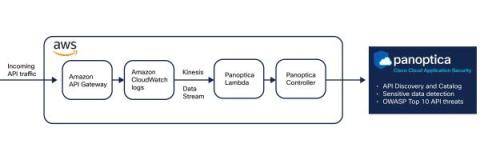
Secure incoming Amazon API Gateway traffic with Panoptica
Enhancing Developer Experience and Security Reporting on Workflows
In our previous blog post, we introduced Bearer’s new GitHub App and highlighted its seamless onboarding process and on-demand scanning capabilities. Today, we focus on how this app can significantly enhance the developer experience within Pull Requests (PRs) while providing critical reporting capabilities to security teams.
Unpacking the Zimbra Cross-Site Scripting Vulnerability (CVE-2023-37580)
On November 16, 2023, a significant security concern was published by Google's Threat Analysis Group (TAG). They revealed an alarming vulnerability in Zimbra Collaboration, a widely-used email hosting tool for organizations. This vulnerability, designated with an identifier, CVE-2023-37580, is a glaring example of a reflected cross-site scripting (XSS) issue. It allows malicious scripts to be injected into unsuspecting users' browsers through a deceptively simple method: clicking on a harmful link.
2023 API Security Trends for Energy and Utilities
As environmental consciousness increases across the globe, the pressure on energy and utilities companies continue to intensify. The global community now understands that how we create and access energy affects geopolitical dynamics, food sourcing, climate change and other concerns that will literally dictate the course of human history. To meet these challenges, the energy and utilities sector is now embracing digital transformation.
APIs - The Hidden Cause of Data Breaches
Introducing Bearer's GitHub App
We are thrilled to introduce the Bearer GitHub App, a powerful addition designed to streamline your workflow and elevate your security practices.
2023 API Security Trends for Government and Public Sector
It’s no secret that government agencies have a tendency to work in silos. If you aren’t familiar with the phrase, it basically means they work in isolation from one another. And if that posed issues before 2020, the COVID-19 pandemic definitely laid bare the need for greater collaboration between public sector organizations – the type of collaboration made possible by application programming interfaces (APIs).
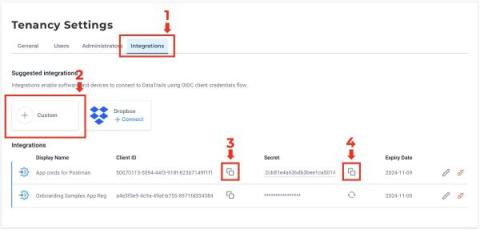
Postman Configuration for DataTrails
One of my favourite tools for playing with REST APIs is, of course, Postman. It can make interacting with DataTrails super quick and easy, and help you develop custom workflows for storing and validating your digital provenance and audit trails. Here’s a step-by-step guide to getting a robust Postman set-up configured, and if you head over the Postman public collections you’ll find a link to a pre-baked DataTrails Postman collection with this done for you, along with some example requests.