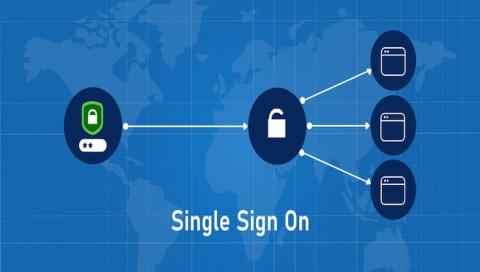
(Re)Discover the Hidden Value of Single Sign-On
Modern zero trust is an information security model that denies users and devices access to applications, data, networks, and workloads by default. One of the optimal ways to help reduce credential-based attacks with applications is to leverage single sign-on (SSO) as part of your access management strategy. SSO combines simplicity with security by removing friction for users to access applications and reducing the administrative overhead and risks for IT associated with password management.