Analysis: A new ransomware group emerges from the Change Healthcare cyber attack
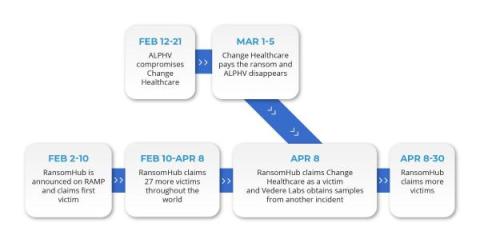
As the full scope of the Change Healthcare cyber attack and ransomware story unfolds, a new leading gang has emerged known as ‘RansomHub’. This ‘new’ group has been claiming more victims since the massive February ransomware and data breach attack. On April 8, Forescout Research – Vedere Labs obtained samples used by RansomHub affiliates in a separate incident.