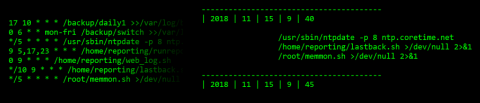
The Art and Science of Secure Coding: Key Practices that Stand Out
Flaws in code lines, file system and data input methods make up the core security vulnerability of any application. This is what we address through secure coding practices. Secure coding guidelines stand out as the last battling army before the enemy line of security risks and threats.