3 Critical Elements of Effective Insider Risk Management
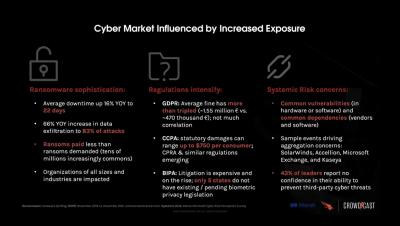
Whether businesses are grappling with rapidly changing market conditions, continued pandemic disruptions, geopolitical conflicts, or shifting workplace arrangements, threat actors are looking to take advantage of the moment to undermine network integrity or compromise data privacy. In many ways, their efforts are bearing fruit. According to a recent industry survey, 66 percent of respondents indicated they experienced a ransomware attack in 2021, a 29 percent year-over-year increase.