Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevSecOps
DevOps Midwest - A community event full of DevSecOps best practices.
DevOps Midwest 2023 brought together experts in scale, availability, and security best practices. Read some of the highlights from this DevSecOps-focused event.
RKVST Track and Trace Demo
Top 5 uses of blockchain in supply chain
It’s April, designated National Supply Chain Integrity month by CISA, NCSC, ONCD and Department of Defense, to promote resources, tools, and information to help organizations and agencies secure their supply chains and build resilience. But what role does blockchain play in supply chain and how easy is it to implement? Blockchain technology has numerous potential applications in supply chain due to its ability to provide a secure, transparent, and tamper-proof ledger of transactions.
RKVST showcases supply chain integrity, transparency and trust implementation at IETF 116 Hackathon
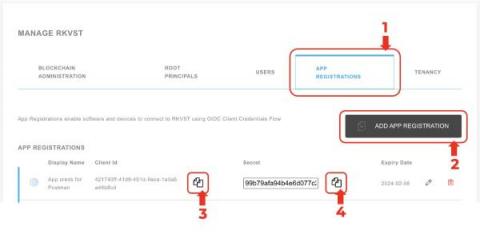
Postman Configuration for RKVST
We’re very pleased with our Python SDK, Jupyter Notebooks, and our OpenAPI Developer Console but sometimes we all want a bit more fine control or command chaining than those can offer. One of my favourite tools for such situations is, of course, Postman. It can make interacting with RKVST super quick and easy, and help you develop custom workflows for storing and validating your digital evidence ledgers.
JFrog DevSecOps Triple Therapy
Learn more about bringing your Dev, Sec and Ops Teams together at https://jfrog.com/