Protecting your GCP infrastructure at scale with Forseti Config Validator part three: Writing your own policy
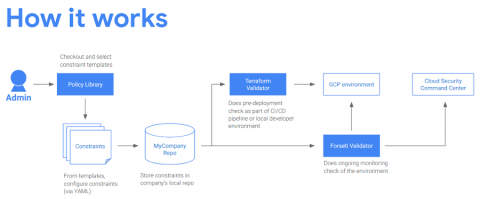
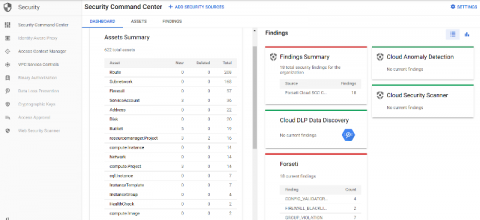
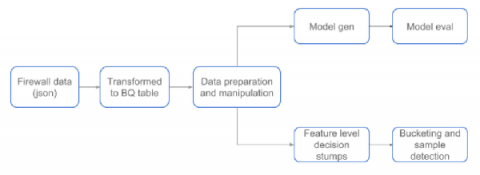
No two Google Cloud environments are the same, and how you protect them isn’t either. In previous posts, we showed you how to use the Config Validator scanner in Forseti to look for violations in your GCP infrastructure by writing policy constraints and scanning for labels. These constraints are a good way for you to translate your security policies into code and can be configured to meet your granular requirements.