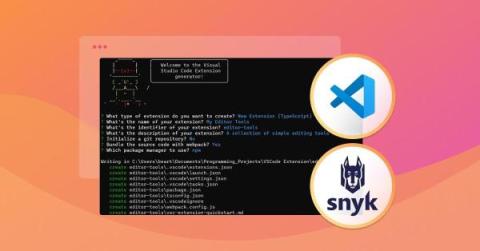
Snyk welcomes Reviewpad: Code, commit, celebrate!
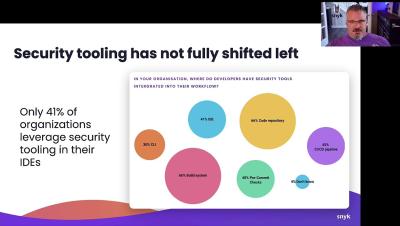
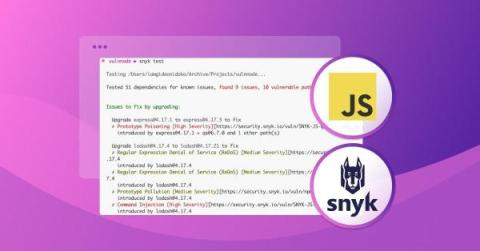
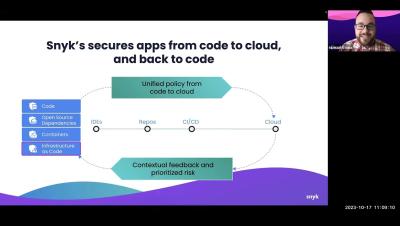
Snyk was founded with the mission of building security products that developers actually want to use. It's how we began and it's that North Star that still drives us today. For security to work at the speed and scale of the modern security development lifecycle (SDLC), developers need tools that integrate seamlessly into the flows they use every day, providing intuitive, actionable feedback along the way.