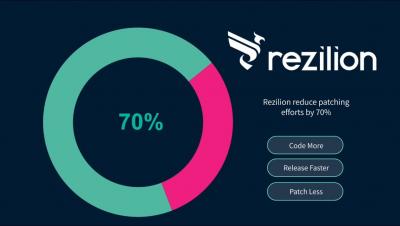
You've Discovered a Vulnerability-Now What?
Identifying a weakness or an imminent threat is not the same as resolving the problem. Inaction is not an option. Or to put it another way, taking a deer-in-the-headlights approach does not work well in the cybersecurity realm. Security leaders and teams, and the DevSecOps units they work with, need to focus on taking action as soon as possible once they have found a vulnerability using a scanner, application security testing, penetration testing, or some other method.