Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
MITRE ATT&CK
It's Time to Do Better as an Industry with MITRE Evaluations
We couldn’t be prouder that CrowdStrike achieved the highest coverage across the last two consecutive MITRE Engenuity ATT&CK® Evaluations. We achieved 100% protection, 100% visibility and 100% analytic detection coverage in the Enterprise Round 5 evaluation — which equates to 100% prevention and stopping the breach. We also achieved the highest detection coverage in the Managed Security Services Providers testing.
MITRE ATT&CK: Your Complete Guide To The ATT&CK Framework
Scarleteel 2.0 and the MITRE ATT&CK framework
In this blog post, we will take a comprehensive dive into a real-world cyber attack that reverberated across the digital realm – SCARLETEEL. Through an in-depth analysis of this notorious incident using the MITRE ATT&CK framework, we aim to unearth invaluable insights into the operational tactics of cyber adversaries.
BAS and MITRE ATT&CK - Basics and Beyond
In 2013, MITRE created the ATT&CK framework to give security practitioners a shared language for the tactics, techniques, and procedures (TTPs) employed by advanced persistent threat (APT) groups. The result is a knowledge source that provides valuable threat information, allowing teams to take a proactive approach in identifying and mitigating potential cybersecurity threats. Though the framework is widely used, most organizations struggle to effectively utilize it.
CrowdStrike Teams with the MITRE Engenuity Center for Threat-Informed Defense in Development of TRAM II
The MITRE ATT&CK framework provides the cybersecurity industry with a common language for describing adversary behaviors, making it invaluable for organizations building or operating cyber defenses, as well as advancing research across the threat landscape.
Sumo Logic Customer Brown Bag - Security - MITRE ATT&CK - August 15, 2023
Using Mitre Att&CK with threat intelligence to improve Vulnerability Management
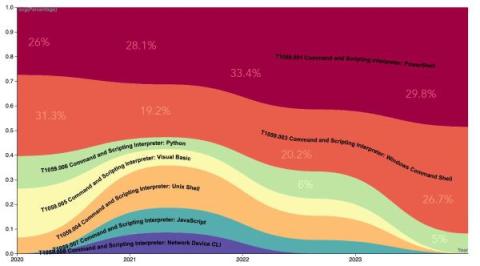
MITRE ATT&CK® is a globally accessible knowledge base of 14 adversary tactics and over 500 techniques based on real-world observations. The first model was proposed in 2013 and publicly released in 2015 which has been gathering momentum over the last couple of years.
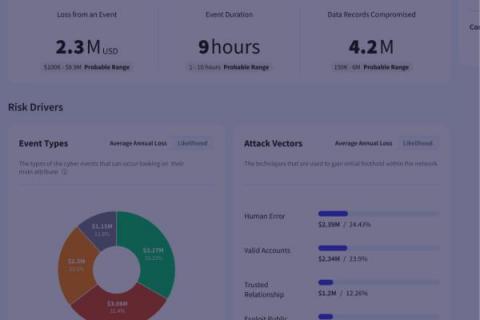
New Feature: Risk Evaluation
Identify Gaps and Thwart Attacks with Devo Exchange and the MITRE ATT&CK Framework
The MITRE ATT&CKⓇ framework holds immense value in the realm of cybersecurity. With its comprehensive and structured approach, it serves as a powerful tool for understanding and countering complex, multi-vector cyber threats.