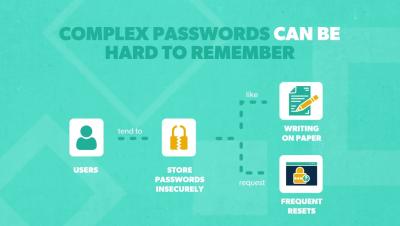
Step-by-step configuration of Files & Folders Recovery
File-level recovery is a great feature of BDRSuite, It allows you to perform granular restores of files or folders from the backed up disk. Watch this video and learn how quick and easy it is to setup and facilitate a granular recovery.