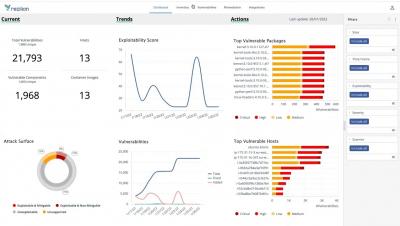
Comparing Source Code Analysis and Software Components Analysis
Finding vulnerabilities in software is serious business. Weaknesses in software can lead to security risks such as costly ransomware or phishing attacks, and there are new types of vulnerabilities emerging all the time. The shift to remote and hybrid work models during the past two years has made vulnerability management even more complex—and necessary. Plenty of products are available to help organizations and development teams find vulnerabilities.