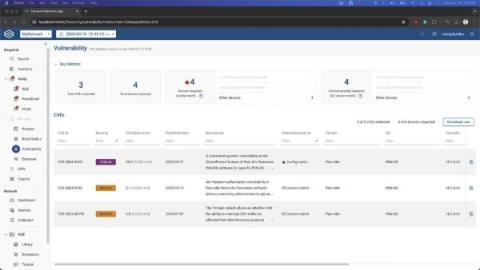
Palo Alto Networks Vulnerability: CVE-2024-3400
On April 12th, Palo Alto Networks released a CVE advisory for CVE-2024-3400, a critical vulnerability identified in the GlobalProtect Gateway feature of PAN-OS, the operating system for Palo Alto Networks firewalls. This command injection vulnerability allows unauthenticated attackers to execute arbitrary commands with root privileges on the affected devices.