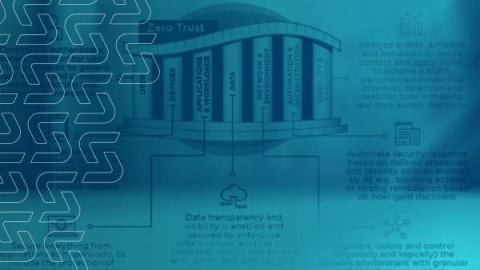
The Role of UEBA in Zero Trust Security
As cyber threats have grown in sophistication and frequency, a paradigm shift in security strategy has become imperative. This shift has given rise to the Zero Trust Security Framework, an approach that challenges the very foundation of trust in network security. User and Entity Behavior Analytics (UEBA) steps into the spotlight as a dynamic force that complements and enhances the Zero Trust Security framework. Let’s discover how UEBA can help organizations achieve zero trust security!