Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Insider Threats
The latest News and Information on Insider Threats including employee monitoring and data privacy.
EP 34 - How to Catch a Malicious Insider w/ Eric O'Neill
Today’s episode of Trust Issues focuses on spycatching! Eric O’Neill, a former FBI counterintelligence operative and current national security strategist, joins host David Puner to discuss his legendary undercover mission to capture Robert Hanssen, one of the most notorious and damaging spies in U.S. history.
New DLP Tools, Location Insights, Track Network Drives, and More! (v9.0) | CurrentWare
Major Supply Chain Cybersecurity Concerns and 7 Best Practices to Address Them
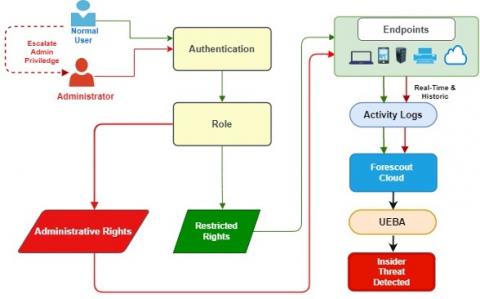
Five Workforce Trends That Intensify Insider Threats
Insider threats don’t often seem like threats at all. They look like colleagues working diligently at the office, logging on to the corporate network from Starbucks or providing a critical third-party service. But insider threats are a big problem that’s getting even bigger and costlier to tackle.
Coffee Talk with SURGe 2023-AUG-22: Ivanti, Citrix, Space Industry, Tesla Insider Threat, Quantum
Work From Home, Quiet Quitting, and How Insider Risk Has Changed
March 2023 marks approximately three years since the world shut down at the beginning of the Covid-19 pandemic. Since then, organizations have seen their workforce change considerably. What was originally a short term plan to work from home has become ingrained in our new work culture. According to a recent LinkedIn poll, at-home work is ticking back up. Only 50% of workers are in the office full-time, the rest work from home full-time or have a hybrid schedule.
Data Loss Prevention (DLP) Systems: Types, Key Features, Pros and Cons
New DLP Tools, Location Insights, Track Network Drives, and More! (v9.0)
CurrentWare version 9.0 is here! This update introduces Advanced HTTPS transparent packet filtering technology, allowing for significant enhancements to the tracking and restriction capabilities of the CurrentWare Suite. By upgrading to CurrentWare v9.0 you will have greater protection against the data security risks of cloud storage services, potentially malicious file downloads, network share drives, and more!